Dear Customers,
A new security vulnerability, CVE-2025-55182, has been disclosed, allowing unauthenticated Remote Code Execution (RCE) in environments using React Server Components. This vulnerability has been rated Critical (CVSS 10.0) and can be exploited across various development frameworks and service environments, requiring immediate attention.
■ Overview
– CVE ID: CVE-2025-55182
– Severity: Critical (CVSS 10.0)
– Affected Range and Fixed Versions: (details to be referenced in the table)
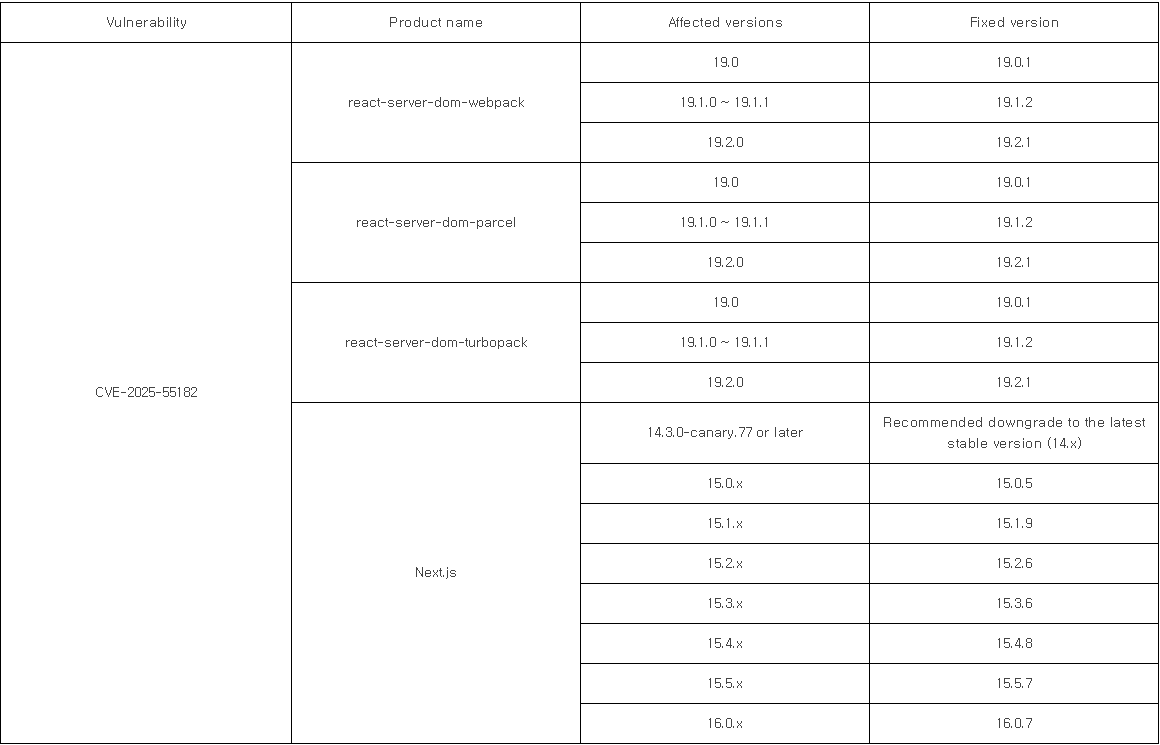
(* Reference: NVD – CVE-2025-55182 )
■ Recommended Actions
– Project Review
: Check the versions of React and Next.js currently in use and verify whether any vulnerable versions are deployed.
– Apply Security Patches (refer to the table above)
: For React, update to version 19.01 / 19.1.2 / 19.2.1 or later.
: For Next.js, update to 15.05 or later, or 16.07 or later.
■ How to Identify Vulnerable Components in Sparrow Cloud
Sparrow Open Source(SCA) can automatically detect vulnerabilities and identify risky components.
1. Dashboard
– After connecting to Sparrow Cloud, click the “Add Project” button on the first screen to create a new project for analysis.
2. Add a project
– Enter the project name and click the “Add Project” button to create the project.
– Click the “Start Analysis” button, upload the source code compressed file or Git URL, and the analysis will begin.
(To analyze a Git repository, you must first authenticate with Git in “Modify Project”)
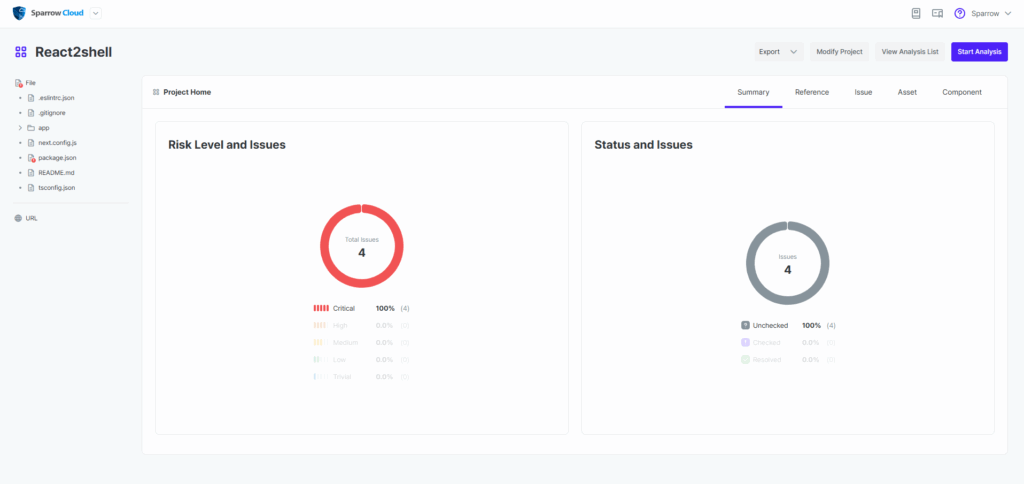
3. Project Dashboard
– Once the analysis is complete, you can check the total number of vulnerabilities and risk level on the project dashboard.
4. Component tab
– Automatically identifies all components included in your project in the “Component” tab.
– You can check if the following vulnerable packages exist here:
- next
- react-server-dom-parcel
- react-server-dom-turbopack
- react-server-dom-webpack
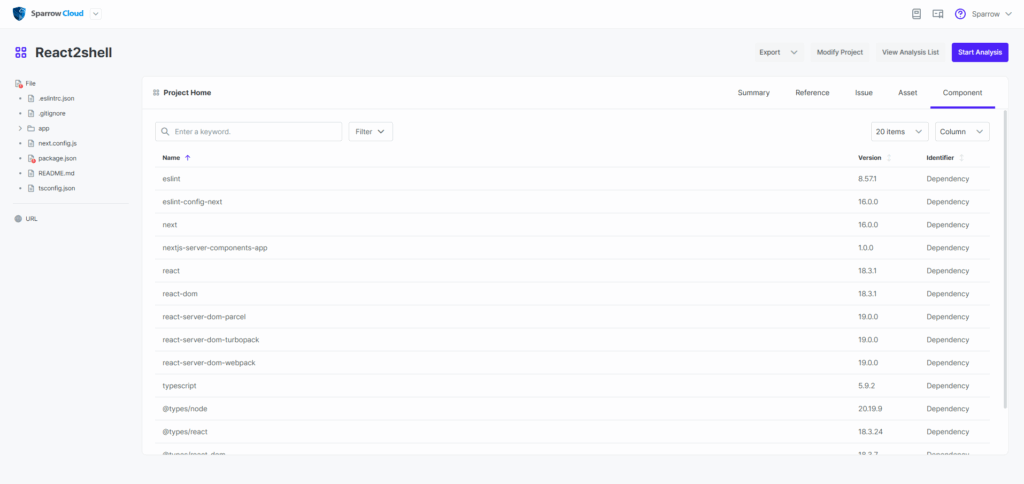
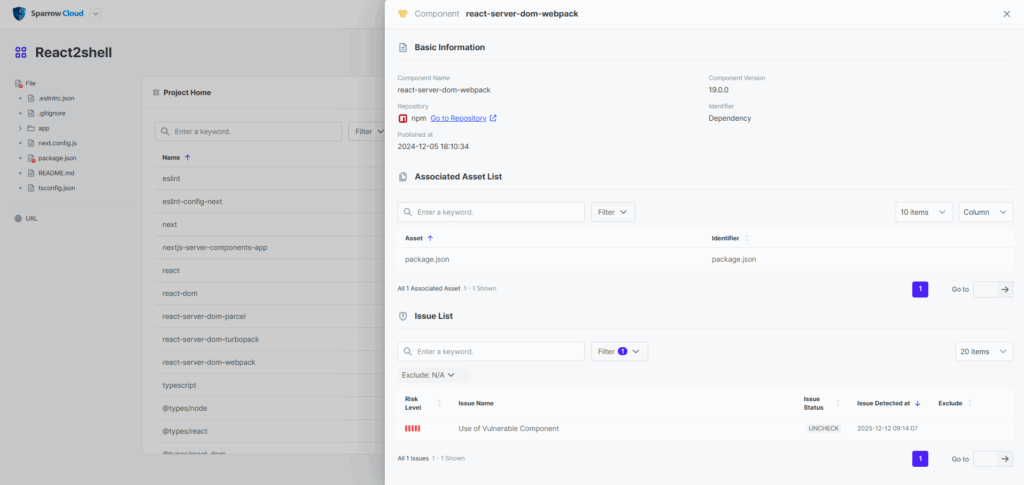
5. Component Details (Next.js)
– Click on the component name to view detailed information.
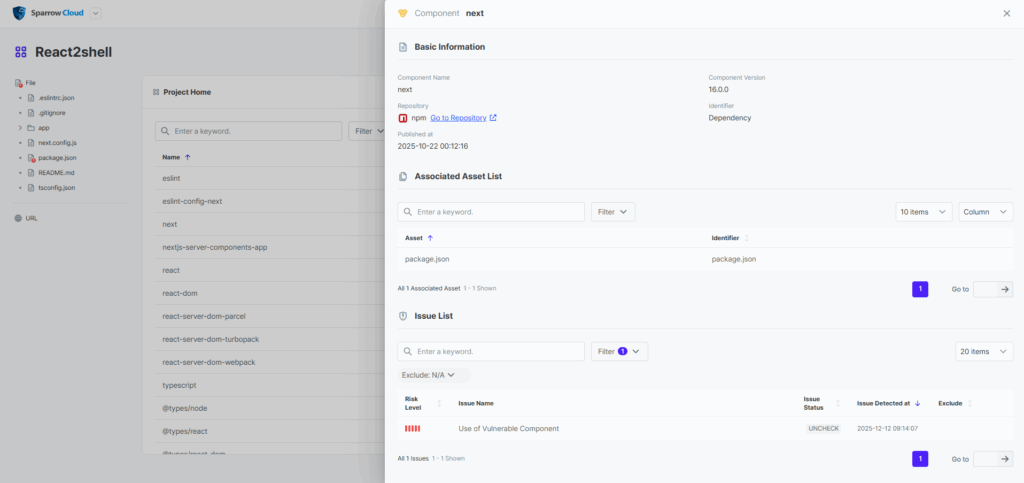
5-1. Component Details (react-server-dom-parcel)
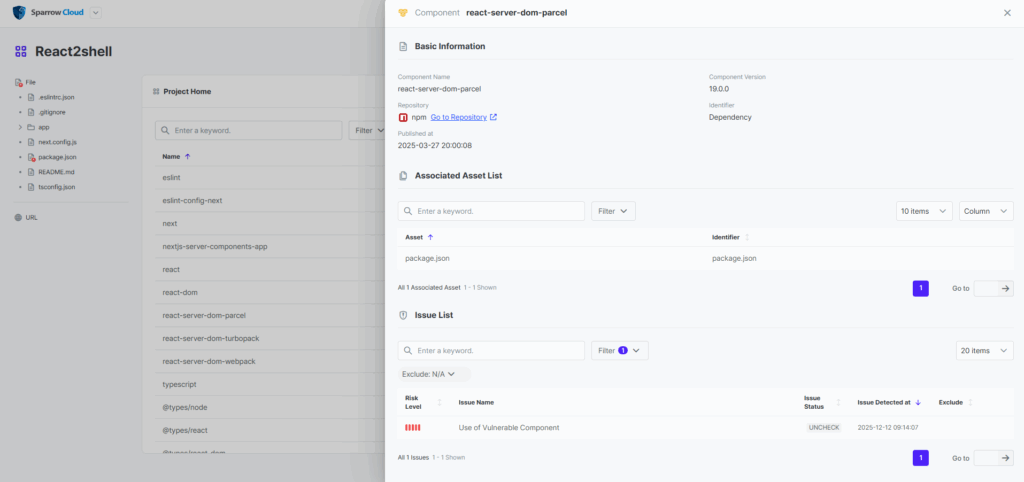
5-2. Component Details (react-server-dom-turbopack)
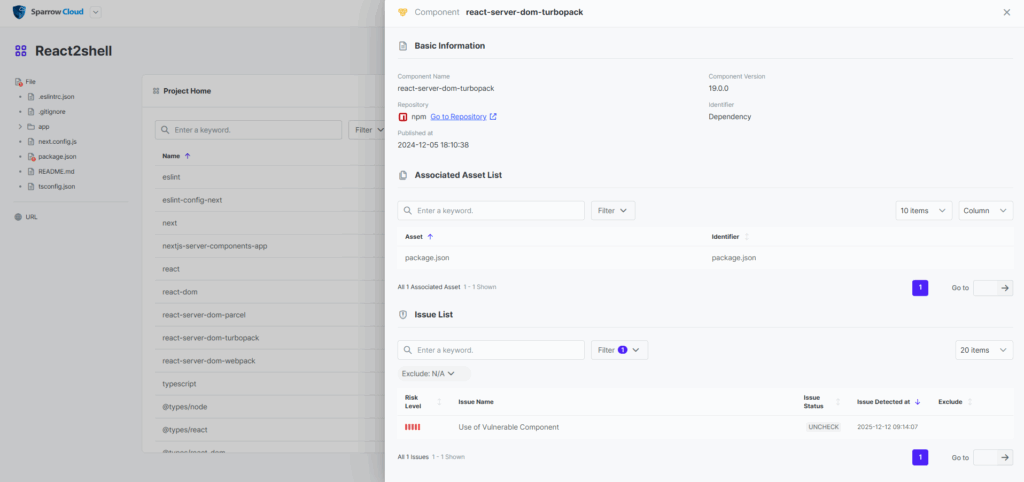
5-3. Component Details (react-server-dom-webpack)
This vulnerability has been actively exploited shortly after disclosure, with actual intrusion cases already reported.
Prompt environment validation and timely patch application are essential.
Sparrow will provide full support to help minimize any potential impact on your organization and to ensure stable service operations.
If you have any questions, please feel free to contact: marketing@sparrow.im





